SCADA Security is a Mindset - ISSSource Explains Why at Belden Design Seminar
For those of us passionate about industrial security it is great to see it being integrated into networking training as it was at the Belden Industrial Ethernet Infrastructure Design Seminar held near Chicago earlier this week.
At this event end users, Systems Integrators and channel partners learnt about industrial Ethernet networking by attending a wide range of lectures and hands-on labs. There were several sessions and labs on industrial security, and the luncheon speakers on each of the first two days focused on security.
Greg Hale, the Editor and Founder of ISSSource.com (a publication we recommend) spoke yesterday and he brought forward a number of interesting points on the cost of cyberattacks, the need for employee training and awareness, and vigilance.
Greg Hale at the Belden Industrial Ethernet Infrastructure Design Seminar, held in Wheeling, IL, Oct 1-3, 2012.
The Cost of Cyberattacks – Can You Afford NOT to Deploy Best Practices?
There is a spectrum of awareness and capability regarding cyber security in industry, with the oil and gas sector being at the forefront of implementing best practices and many other sectors still unconvinced that it merits expenditure and resource allocation.
According to Greg companies that implement cyber security best practices are 2.5 times less likely to experience a major cyberattack and 3.5 times less likely to experience unplanned downtime than companies that don’t. Cyber incidents cost organizations:
- $558,000 in revenue losses
- $480,831 in brand damage
- $366,301 in compliance fines
- $174,309 in lost productivity
It all adds up to costing U. S. industry $6 million a day or $20 billion a year.
These are costs that go straight to the bottom line and they are accompanied by other costs that are harder to quantify such as the loss of a business’ Intellectual Property (IP).
Those organizations still thinking of cyber security as a type of insurance that they don’t need, might have been chastened by the words of another presenter, Mark Cooksley. Mark recently moved into a new role at Hirschmann, Belden’s industrial networking group, but for many years he was the Product Manager for Security.
He recounted in his session on network security the numerous times he had been called onsite to help customers who were recovering from a cyberattack. The use of best practices such as segmenting the control network into zones of devices with similar security requirements (as per ISA IEC standards) and controlling communication between zones with industrial firewalls would have minimized damage to the affected organizations.
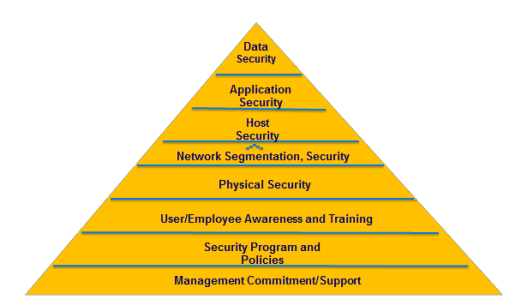
Defense in Depth includes Employee Training and Awareness
Another Belden speaker, Jeff Cody, gave a good presentation on Defense in Depth that included things like physical security, switch security, network security, redundancy etc. These are measures that involve the physical environment and the industrial network, and they are important.
Greg took it a step further in his talk by including the following in his Defense in Depth model:
- User/employee awareness and training
- Security programs and policies
- Management commitment and support
The Layered / Defense in Depth Model shown by Greg Hale of ISSSource.com in his presentation at the Belden Industrial Ethernet Infrastructure Design Seminar.
These measures that focus on the human side of the security equation are equally as important as the physical and networking measures. For instance, Greg gave the example of a Xerox study that revealed that more than half (54 percent) of employees don't always follow their company's security policies - leaving the security of sensitive data at heightened risk.
A Cisco data breach study found that employees fail to adhere to security policies due to a lack of understanding and poor communication from their security department.
Mark Cooksley echoed this theme with his comments on organizations needing to know the decision making path for dealing with a cyberattack. Who makes the call on disconnecting the plant network from the enterprise network or the Internet, for example? Inaction because of unclear authority could lead to increased damage.
The Need for Cyber Vigilance
Another point that Greg made was the need for an ongoing cycle of:
- Business Risk Assessment
- Vulnerability and Security Assessment
- Vulnerability Management & Remediation
- Policies and Procedures Standardization
- Incident Response Planning and Management
- Security Awareness & Training
- On-going Security & Network Monitoring; Security Tools Implementation/Support
This is similar to the best practice we developed with exida, the “7 Steps to ICS Security”.
It is a practice that the leaders in cyber security are careful to maintain. For example, last week I wrote about the Shamoon malware that attacked and destroyed data on an alleged 30,000 computers at the largest energy company in the world, Saudi Aramco.
It was a very destructive and disconcerting attack and one whose ramifications we are continuing to follow. Greg brought forward the comments of Saudi Aramco’s CEO, Khalid Al-Falih, post-Shamoon:
“Saudi Aramco is not the only company that became a target for such attempts, and this was not the first nor will it be the last illegal attempt to intrude into our systems, and we will ensure that we will further reinforce our systems with all available means to protect against a recurrence of this type of cyber attack.”
Saudi Aramco knows that they are a particularly attractive target for attackers. Likely their cyber security practices are already top notch; nonetheless they experienced a serious breach and have to go through the cycle of improving their defenses even further.
SCADA Security is a Mindset
Greg summed up industrial security as: “A program of strategies, procedures and controls to protect sensitive information [and processes] against unauthorized disclosure, transfer, modification, or destruction.” If your organization does not have a strong culture around cyber security, Greg’s presentation may help you change that. Let us know your thoughts on Greg’s key points.
Related Content to Download
|
Presentation - "Industrial Security is a Mindset" |
Related Links
- ISSSource.com Home Page
- Belden.com Webpage: 2012 Industrial Ethernet Infrastructure Design Seminar
- Belden.com Webpage: Belden’s Industrial Ethernet Infrastructure Design Seminar Opens to Record Attendance
- Belden.com Blog: Industrial Infrastructure that Works
- Blog: Simpler SCADA Security Beats More User Training
- Blog: Shamoon Malware and SCADA Security – What are the Impacts?




Comments
Design
How can we discuss ICS design if we do not discuss the basic constructs of every security design. Security zones, conduits and channels. Technical cyber security is all about attack surface reduction and attack surface hardening. Security zones, conduits and channel analysis are the key instruments. Understanding how to apply these instruments and their rules is what it is all about.
And ofcourse security principles such as least privilege, layered defense, fail to secure state, check at the gate and many more do apply on every design decision. I am sorry to say but Greg Hale's model is primarily a marketing picture if this needs to show what a layered defense is, from a security design perspective of an ICS it doesn't add anything.
I am sorry to say but the event never touched the core of security design. Topics discussed were topics of the past.
Design
I’m sorry you did not find value in Greg Hale’s presentation or the Belden Design Seminar. Greg’s presentation was not a technical one, but one that I felt brought forward good information on cyber security for the audience, which were mainly people without a lot of experience in designing and implementing security measures. The illustration he provided for Defense in Depth is high level, and is useful on that basis. Hopefully people reading this blog will look further for in-depth information we have provided on Zones and Conduits, Securing Systems from APTs, Why Firewalls Need to be Stateful etc.
Regarding the topics at the Belden Design Seminar being discussed as topics of the past, I agree that they were not leading edge, but they were not irrelevant either. A lot of good, practical advice was given at the 3 talks and 1 hands-on lab that I attended on security.
Thank you for taking the time to comment.
Relevance
I didn't mean to say irrelevant, but not the core issues of a DESIGN seminar. But ok, mybe my expectations were different from your objectives. This can happen, it wasn't a lost day.
Add new comment