Defense in Depth is Key to SCADA Security - Part 1 of 2
In my blog article on the Factory of the Future I mentioned the concept of Defense in Depth. This is such a critical foundation in the field of security that I am going to dedicate a number of columns over the next few weeks to this topic.
The first thing to understand is that it is not a cyber security concept. It is a core concept in the entire practice of security, starting with the ancient Chinese military sage Sun Tzu. Countless battles have been lost because the law of “defense in depth” has been ignored.
In fact Carl von Clausewitz, a Prussian soldier and military theorist during the Napoleonic era stated: "If you entrench yourself behind strong fortifications, you compel the enemy to seek a solution elsewhere." So let’s explore this idea and begin by looking at a military example where defense in depth was not used.
The End of the Great War Led to a Fortress Mentality
Imagine it is November 1918. World War I, the greatest war the world has ever seen, has just ended and France is reeling from the devastation. The conflict has killed over one million French citizens, wounded a further four million and destroyed much of the countryside of eastern France. A fierce debate begins to rage - “how should France ensure that another invasion of their beautiful country by the German hordes never occurs again?”
While there are a number of opposing ideas on how to achieve this, the one that prevailed is to build a defensive line of fortresses along the border with Germany.
|
Thus, between 1930 and 1936, the French government poured approximately three billion francs into building 400 miles of fixed concrete fortifications known as the Maginot Line. Everyone in France felt secure knowing that their country was safe behind the massive barrier of concrete and guns. Then on May 10th 1940, Hitler attacked France. |
 |
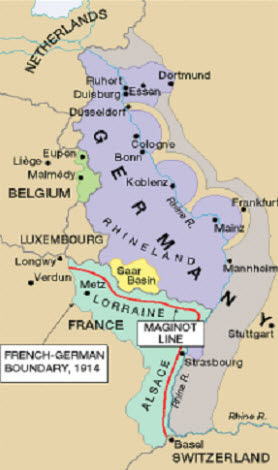 |
While a German decoy force sat opposite the Line, Hitler’s second Army Group cut through Belgium, the Netherlands and the undefended Ardennes Forest. These troops completely bypassed the Line, within a week Nazi troops were deep inside France, and a month and half later France surrendered. The Line is only marginally involved in the fighting. What went wrong? The Line certainly achieved the task it was intended to do, namely preventing a direct assault against France's eastern border. But France's strategic use of the Line was poor. As originally designed, the Maginot Line was supposed to be only part of a larger multilayered plan, involving other defenses and the French Army. |
Instead the mere existence of the Line gave French authorities a false sense of security. They based their entire defense strategy on this single solution, resulting in a quick and embarrassing defeat at the hands of the Nazis.
A Single Method of Defense Leads to Single Point of Failure
In the words of several historians “The Maginot Line did not fail France, but the ‘Maginot mentality’ did cause her defeat.” It was the belief that a single very strong defence was good security.
Basing a security design on hiding behind a single monolithic solution is called the Bastion Model and results in the possibility of a single point of failure. With the inevitable help of Murphy’s Law, this single point will eventually either be bypassed (like the Maginot Line) or will experience some sort of malfunction. When it does, the system will be left wide open to attack.
In the same way, industrial security designs that assume all evil traffic will flow through a single choke point are succumbing to the same dangerous set of beliefs. Depending on a single firewall or data diode is building a security solution based on a single point of security failure. Only a proper defense in depth design, where the control devices and systems are both individually and collectively hardened, can provide reliable security for the plant floor.
In a future blog we will look at the alternative to the Maginot mentality. We will see how sound security strategy, regardless of whether it is military, physical or cyber security, is based on the concept of layering multiple security solutions, so that if one is bypassed, another will provide the defense.
Related Content to Download
Note: you need to be a member of tofinosecurity.com and logged in to have access to the document below. Register here to become a member.
|
White Paper - "Effective OPC Security for Control Systems"
|
Related Links about Military Security
- OoCities.org: Brief History of the Maginot
- Wikipedia: Carl von Clausewitz
- Wikipedia: Sun Tzu
Related Links about ICS and SCADA Security
- Defense in Depth: Layering Multiple Defenses - Part 2 of 2
- Antivirus Protection for SCADA Security - A Silver Bullet?
- Factory of the Future meets Stuxnet’s Children: Egad!
- Case Profile: Davis-Besse Nuclear Power Plant
- New SCADA Security Reality: Assume a Security Breach
- asian-power.com: The new paradigm for utility information security: assume your security system has already been breached



Comments
Defense in depth
Interesting comparison, though I am not certain if the comparison with the Maginot line failure is a failure of defense in depth. Just as important as the defense in depth concept, is the need for reducing the attack surface to a minimum. With the Maginot line the french " forgot" to protect their north side, very similar to what we see in ICS .... Multiple points of entry and insufficient hardening, so too large attack surface.
Another interesting comparison would be the German attack on Holland.Where the Dutch army expected to be safe behind a water line to stop the German troops, a new concept made this century old defense worthless. the German paratroopers just flew over the defense and were dropped into the ""secure" area.
Not very different from a client side attack fully ignoring all firewalls and other perimter defenses - air gaps included- and just jump directly into "secure" area with new methods of attack. And a good lesson that you can't just build a secure defense and not continuously adapt it to meet new threats.
Plausible analogies
Plausible analogies, indeed. In the SCADA world, you can often hear things like: We operate a firewall, we must be secure; internal attacks were are not even considered. What a misconception.
Failure of Imagination
It is said that the Maginot Line was constructed in a flawed manner. It was, it could be said, a great example of a failure of imagination. That said, the protecting of today's SCADA and other critical infrastructure also needs to consider this failure of imagination. The comment above from Anonymous are spot on. The threat are evolving faster then the industrial and utility industries are used to.
Are we heading to a day of reckoning, where the forces of cyber crime and state sponsored forces overwhelm and erase the good things that information technology delivers? If we head down our current path of incremental, individualized approaches to SCADA cyber security, the answer is “Yes.” That said, I’m an optimist and believe that if the security professionals of the world can work together and share information, we stand a good chance of protecting our critical infrastructures.
Add new comment