SCADA Security Breached at U.S. Water Utilities
Last week Joe Weiss caused a bit of a storm by releasing information on a cyber attack on the water SCADA system at the Curran-Gardner Township Public Water District, in Illinois. Now it seems like a second water utility has been hacked, this time in the City of South Houston.
If you haven’t been following the events, Joe first posted a blog article on November 17. He then read Wired Magazine and KrebsOnSecurity sections of a report by the Illinois Statewide Terrorism and Intelligence Center:
“Sometime during the day of Nov. 8, 2011, a water district employee noticed problems with a SCADA system. An information technology service and repair company checked the computer logs of the SCADA system and determined the system had been remotely hacked into from an Internet provider address located in Russia…
Over a period of 2-3 months, minor glitches have been observed in remote access to the water district’s SCADA system. Recently, the SCADA system would power on and off, resulting in the burnout of a water pump.”
Two U.S. Water Utilities Hacked in the Same Month
It is believed that the attackers breached the IT systems of the company that either manages or makes the SCADA systems used at Curran-Gardner and stole customer usernames and passwords. The attackers then used this information to infiltrate the Curran-Gardner SCADA system.
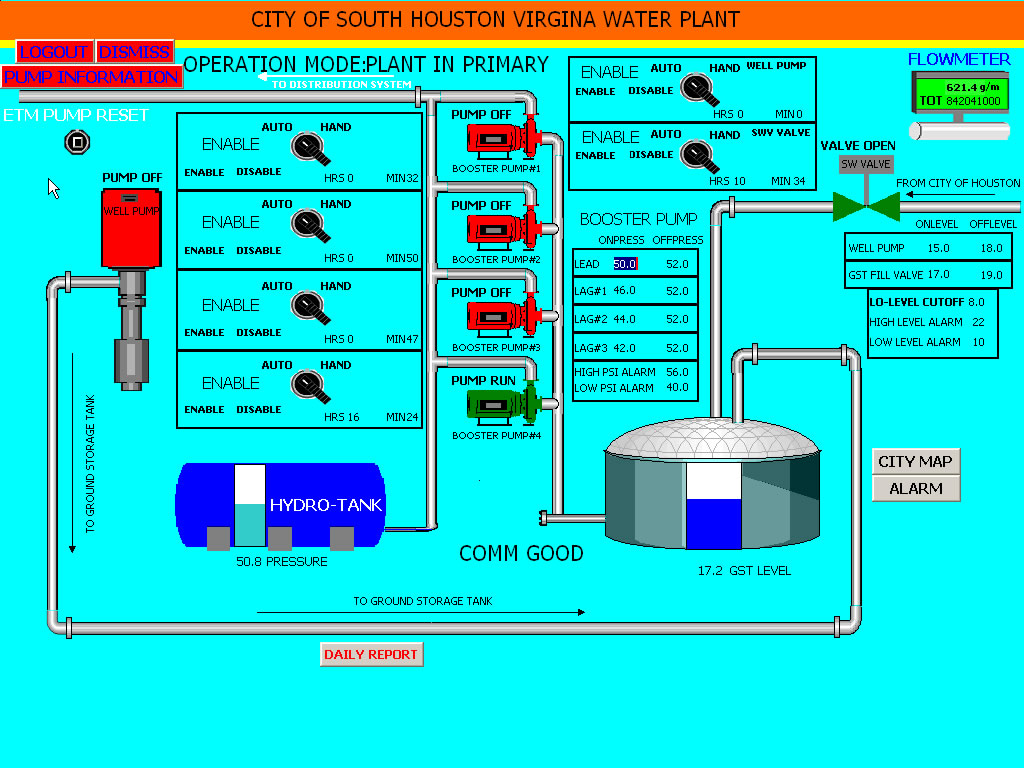
The ink wasn’t dry on Joe’s news when a twenty-something hacker using the name “pr0f” or “@pr0f_srs” published information of a successful penetration of the South Houston Water Utility. This attacker used an unrelated technique to gain access to the water utility and then posted several screenshots of the control system on PasteBin, including this one:
Water Utility Attacks were Friendly – This Time
Pr0f makes it very clear that his was not a malicious attack, only a proof-of-concept to show that many SCADA systems are very insecure:
“I dislike, immensely, how the DHS tend to downplay how absolutely (expletive deleted) the state of national infrastructure is. I've also seen various people doubt the possibility an attack like this could be done. So, y'know … the city of South Houston has a really insecure system. Wanna see? I know ya do.”
“I'm not going to expose the details of the box. No damage was done to any of the machinery; I don't really like mindless vandalism. It's stupid and silly.”
“On the other hand, so is connecting interfaces to your SCADA machinery to the Internet. I wouldn't even call this a hack, either, just to say. This required almost no skill and could be reproduced by a two year old with a basic knowledge of Simatic.”
(oh no – looks like Siemens is back in the news again…)
Pr0f then wrote a second, very articulate article on PasteBin explaining why he did the attack. He makes some good points:
“It's not as grim and war-like as the media are making it out to be, at all. 'Cyber war' and all of that is little more than hype, and I'd like to address that in a moment. But it is a sign that the security-poor institutional culture in automation needs changing, and needs changing fast…
I would like to go on record and say that the main reason I did what I did yesterday was essentially because I know I am not the only person with an interest in these systems. I also know I am not the only person who has explored them and read up on them. However, at least I am going public (ish) and trying to draw attention to the topic…
I don't think I am alone in suggesting that the gravity of the problem is more serious than ICS-CERT and similar are equipped to deal with. I would love to see some real reform and discussions between the government, manufacturers of ICS, and people who use these systems happening, because there seems to be a huge disconnect between the parties involved.”
The sad fact is that many companies and many industries are still not taking security seriously. Even these two incidents probably won’t be enough of a wakeup call for most companies. I just pray that it won’t take a disaster to get the SCADA users, vendors and government moving toward making our critical infrastructures more robust and secure.
Related Content to Download
Note: you need to be a member of tofinosecurity.com and logged in to have access to the document below. Register here to become a member.
|
Article - "Revealing network threats, fears" |
Related Links
Here are some Practical SCADA Security Articles on Security Vulnerabilities in SCADA and ICS:
- Stuxnet Lesson: Is SCADA/Control Field Device Firmware the Next Malware Target?
- More SCADA Security Threats: Where There’s Smoke, There’s Fire
- The Italian Job – Multiple SCADA / ICS Vulnerabilities Go Public



Comments
What is the manufacturer of the SCADA System
and what default password policy do they have implemented (in GPO).
Sales
The guy posting the article works for a computer security firm. Nothing like a little fear to drum up some business. I’m pretty sure that my 700 series relays will be secure against a cyber attack.
Yes I Work for a Security Firm
You are correct that I work for a security firm. In fact I founded the firm in 2006 with Joann Byres. I used to be a very successful controls engineer, before I got mixed up in ICS/SCADA security.
Now the reasons I created a ICS/SCADA security firm was because I personally saw some bad security events happen to good companies. I also found some very serious security vulnerabilities in main-stream PLCs and DCS that would be easy to exploit. But most important, I saw that no one was doing much to solve the problem. Whatever was suggested was far too difficult to use on the plant floor or in the substation.
Now since I like my power and water reliably delivered to my house every day, I thought I should do something. Tofino Security and the ICS/SCADA firewalls we create was the result. And even with Tofino, I believe that there is still a problem that needs fixing.
If all your control strategy is based off of 700 series relays, you don't have to worry. But if you use RS-232/485, Ethernet, TCP/IP, Windows etc. in any part of control system, you might want to reconsider. I would, but it is completely up to you.
Add new comment