Making SCADA Security Simple with the Schneider ConneXium Tofino Firewall
“Lacking extravagant IT budgets, automation systems also require cyber security systems that just work, with a minimum of human intervention.”
I could not agree more. The above statement is part of a quote from Bob Lockhart of Pike Research that is contained in today’s press release regarding the new ConneXium Tofino Firewall, a new product that we created with Schneider Electric. It speaks to my core belief that in order to make SCADA and ICS cyber security effective, we need to make it easy to deploy, configure and maintain.
That philosophy has been part of the fundamental design of the Tofino Industrial Security Solution since my days in the BCIT lab1. This new joint Schneider Electric/Tofino Security product moves that vision another step forward by introducing a number of really cool ease of use features.
Introducing the Schneider Electric ConneXium Tofino Firewall
|
Last week I talked about the need to address SCADA vulnerabilities now, while at the same time designing security into future control systems products. Kudos to Schneider Electric for taking action on numerous fronts to improve cyber security for their customers. For example, they have taken on the complex and expensive step of performing a detailed security analysis of all their major automation products. Another has been to work with us to create the ConneXium Tofino Firewall. In case you didn’t know, ConneXium is Schneider Electric’s line of network infrastructure products that interoperate with their automation products. The ConneXium Tofino solution is a new product that hardens industrial systems against network incidents and cyber attacks. Like all ConneXium products, it is designed to work seamlessly with other Schneider Electric products. Plug-n-Protect Deployment and ConfigurationAs I mentioned earlier, ease of use was a core goal for the project for both teams. First, we worked hard to make the ConneXium Tofino a solution that can be used out of the box. For example, the user interface for the configuration tool (called the ConneXium Tofino Configurator) is designed to look and feel like Windows Explorer, a tool we all use to manage our files on a PC. Anyone with even basic Windows 7 experience will intuitively understand how to use the ConneXium Tofino Configurator. Another thing you will quickly notice when you start the Configurator are the “Asset Templates”. These are pre-configured templates for major Schneider automation products. Rather than having to be security experts, engineers simply select the models of Schneider products they are using in their plants. They then decide which devices they want to allow communication to, and the appropriate rules for those products are automatically generated. Finally, new expert technology looks through the rules for common mistakes in firewall programming and suggests possible improvements. |
 |
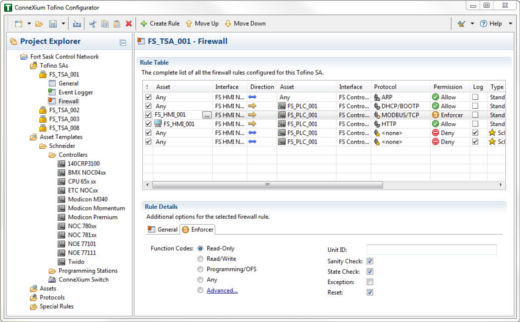
The ConneXium Tofino Configurator is designed to look and feel just Windows Explorer. Here you can see the rules for the Tofino “FS_TSA_001” selected in the Project Explorer. Selecting the “Read-Only” option in the Rule Details configures the firewall to only allow Modbus commands that are data read commands. All data-write and programming commands would be blocked.
Deep Packet Inspection of Modbus TCP Messages
As many of you know, most SCADA and ICS protocols do not provide granularity for the network messages. At the TCP/IP layer, a data read packet looks exactly like a PLC firmware update packet. If you allow data read packets to pass through a traditional firewall, you are also allowing the firmware update packet to pass through. This is a serious security issue.
The ConneXium Tofino addresses this issue by including our Modbus TCP Enforcer module in every unit shipped. The Modbus TCP Enforcer only permits approved Modbus commands from approved devices to pass through the firewall. Known as “Deep Packet Inspection”, this prevents incidents ranging from inappropriate remote programming to deliberately corrupted messages from malware and hackers. Technology like this is a rare capability amongst firewalls.
Again, ease of use for the Modbus TCP Enforcer was critical. Instead of expecting control engineers to know what specific Modbus function codes are used for applications, a number of standard use cases are defined. For example, if you want the ConneXium Tofino to only allow Data Read commands to pass between a PLC and a HMI, then you select the Read Only option.
Tofino Security Profiles for Product Vulnerabilities
In an earlier blog I talked about the need to develop alternatives to the patch tread mill. The ConneXium Tofino Firewall continues this vision by supporting Tofino Security Profiles. These are sets of tailored rules and protocol definitions that defend against newly disclosed vulnerabilities and malware. Each Tofino Security Profile is packaged so that it can be quickly deployed without impacting operations, thereby providing a quick and effective defense against new threats.
For example, last week we released a Security Profile for the CoDeSys vulnerabilities, a security threat that impacts hundreds of different control products. Since CoDeSys hasn’t offered a patch for their products yet, we worked with Joel Langill (www.scadahacker.com) to come up with an immediate mitigation.
Cyber Security that just Works
If you are a regular reader of this blog you know that most of our articles are intended to be educational rather than marketing related. Certainly this one is “tooting our own horn”, so thanks for sticking with it!
But most important, I hope that this blog demonstrates how technology can be designed to make industrial cyber security easy to deploy. Whether you use Tofino technology or not, we hope that you can see how cyber security technology can be delivered so controls professionals can ensure their systems are secure - and still concentrate on their core responsibilities of safe and reliable production.
I will close with more words from Bob Lockhart from Pike Research:
“Automation systems face unique cyber security challenges that require protection, built by companies that understand how those systems work…. Companies want to focus on their core business, not the enabling technology.”
Can you think of more ways to make SCADA and ICS Security easy? Of course we all want security to be designed into controls products, but in the meantime, what tricks or technologies do you use to keep security simple and reliable in your company?
1 In 2001 I founded the British Columbia Institute of Technology (BCIT) Critical Infrastructure Security Centre. It became one of North America’s leading academic facilities in the field of SCADA cyber security.
Related Content to Download
|
White Paper: "Using ANSI/ISA-99 Standards to Improve Control System Security" |
Note: ANSI/ISA-99 Standards have recently been renamed ISA/IEC 62443 Standards.
Related Links re: ConneXium Tofino Firewall
- Press Release: Belden Helps Schneider Electric Secure Critical Industrial Infrastructure
- Schneider Electric PDF: ConneXium Overview Brochure
Other Related Links
- Press Release: Honeywell selects Tofino™ Modbus Read-only Firewall to Secure Critical Safety Systems
- Press Release: Triconex / Tofino OPC Firewall Honored with Breakthrough Product Award from Processing Magazine
- Blog: SCADA Security & Deep Packet Inspection – Part 1 of 2
- Blog: SCADA Security & Deep Packet Inspection – Part 2 of 2
- Blog: Address SCADA Security Vulnerabilities NOW, Not Later (plus White Paper)
 Subscribe to the "Practical SCADA Security" news feed
Subscribe to the "Practical SCADA Security" news feed
Plug-n-Protect is a trademark or registered trademark of Belden Inc. or its affiliated companies in the United States and other jurisdictions. Belden and other parties may also have trademark rights in other terms used herein.


Comments
Product Question
Eric - does the Modbus TCP deep packet inspection cover the Modicon proprietary function code 90? That would be pretty cool if you could filter/create rules on the sub function codes for that powerful function code.
Dale Peterson
Digital Bond, Inc.
Product Question - Modbus TCP Deep Packet Inspection
Currently the Modbus TCP deep packet inspection covers function code 90 to a point, but does not filter sub function codes for FC90. In other words, you can select to either block or allow FC90, but if you decide to allow FC90 between a given master and PLC, then the Tofino allows all FC90 sub functions between that pair of devices. For most devices we suggest that users set the "Function Codes" radio button to Read/Write (see the lower centre of the screen shot in the blog for an example). Then only special masters (such as programming stations) get set to the "Programming/OFS" option that allows FC90.
Full DPI of FC90 was on the wish list for the ConneXium Tofino, but it had to wait until a later release. Getting a reliable security solution to Schneider customers ASAP was the top priority. Expect to see a number of additional features added over the next while.
Roadmap for industrial protocols
Hi Eric,
Is there is road map to include any other industrial protocols?
I thinking in DNP3 and/or IEC104.
Regards
Add new comment