Using Tofino Security to Control Stuxnet - New Application Note
One of the three pathways Stuxnet uses to infect other computers is via the Local Area Network communications inside the control system (the other two are via infected USB drives and via infected Siemens project files).
This blog post addresses how to restrict network-driven infections using the Tofino Industrial Security Solution as the example product for mitigation. Tofino is our own product, so you know where my bias is. However, no matter what technology is deployed, the concepts I will talk about are the same.
Dividing the Control Network into Security Zones
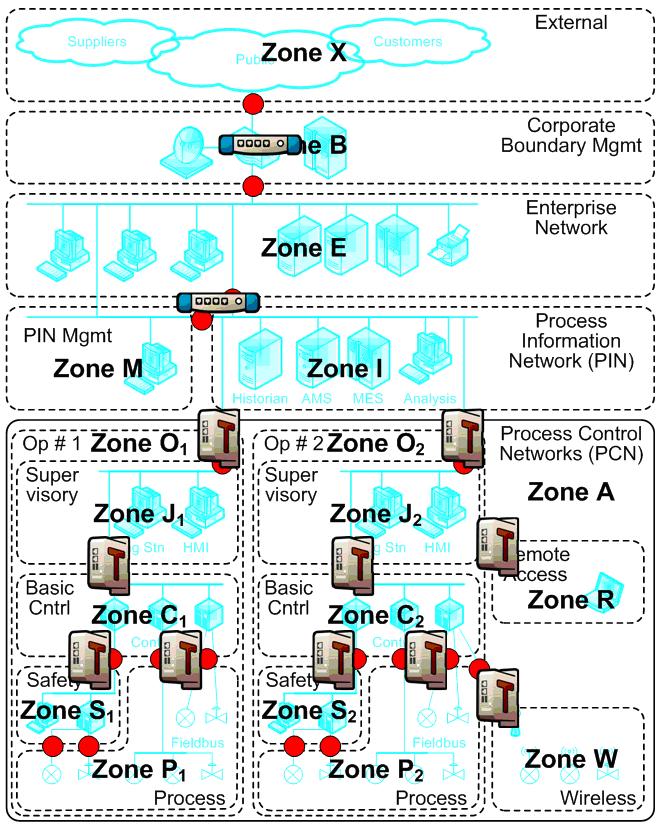
First, in my last blog post I talked about the need to divide up control systems into security zones. If you are not familiar with the security zones concept, I suggest you read that post first.
|
Let’s imagine you agree that dividing up your network into zones of assets with similar security requirements based on factors such as control function, operational considerations and criticality is the way to go… and that you have done the planning work to map out what the zones are. Now you need to install an industrial firewall between the zones and implement rules that block the protocols that Stuxnet uses for infection. Using the Tofino Industrial Security Solution to limit network traffic between zones to only what is needed for the system to operate, begins with deploying Tofino Security Appliances (Tofino SAs) as the conduits between zones. Tofino SAs are industrially hardened and can be installed into live plant networks. |
 |
Blocking the Protocols used by Stuxnet
Each of the Tofino SAs are customized with Loadable Software Modules (LSMs). For Stuxnet control, the following modules are needed:
- Tofino Firewall LSM
- Tofino Secure Asset Management LSM
- Tofino OPC Enforcer LSM
- Tofino Event Logger LSM
Once each LSM is loaded, each appliance is configured to prevent the protocols that Stuxnet uses from passing between zones. In particular three protocols need to be managed: Web (HTTP) traffic, Remote Procedure Call (RPC) traffic and, in Siemens systems, MSSQL traffic.
Note that I say “managed” and not just “blocked”. Unfortunately Stuxnet uses many of the same protocols as valid system applications, so just blocking these protocols will prevent proper operation of the control system.
We’ve prepared an Application Note “Using Tofino to Control the Spread of Stuxnet Malware” which spells out exactly what steps to take to configure Tofino LSMs to control HTTP, RPC or MSSQL traffic between zones. Configuration is straight forward because Tofino is aware of most industrial protocols and thus can propose rules, making it easier to configure by controls engineers.
Testing the Firewall Configurations
After configuring any security device and firewall it is very important to test to make sure that firewall rules do not disrupt industrial processes.
The Tofino Industrial Security Solution provides a Test mode which allows all network traffic to pass, but reports any traffic that would have been blocked by the firewall had it been in Operational mode. We recommend that you run in Test mode for 24 hours before switching to full Operational mode.
Once the Tofino SAs are deployed they provide excellent “watch-dogs” to warn if an infection is occurring.
Controlling Stuxnet
Preventing the spread of Stuxnet over control networks is key to maintaining safe, reliable and secure industrial systems. With a system such as the Tofino Industrial Security Solution, you can mitigate many of the effects of the Stuxnet virus while protecting your industrial network against numerous other methods of accidental or malicious attacks.
Note: you need to be a member of tofinosecurity.com and logged in to have access to this document. Register here to become a member.
![]() Using Tofino to Control the Spread of the Stuxnet Malware - Application Note (485 kb)
Using Tofino to Control the Spread of the Stuxnet Malware - Application Note (485 kb)


Add new comment