Controlling Stuxnet – No More Flat Networks PLEASE. Let's Embrace "Security Zones".
In last week’s post, I mentioned that Eric Cornelius gave a very interesting talk at last week’s ICSJWG meetings. Cornelius works for INL (Idaho National Labs) and they are doing Stuxnet research for the US Government.
I want to highlight some of Cornelius’ comments, as well as other themes that came up that are important for the average SCADA / ICS system engineer or manager.
|
Cornelius’ talk started by providing details on Stuxnet’s design. He highlighted the expert construction of the worm and the very detailed knowledge of Siemens’ S7 technology that the designers possessed. This part of the talk basically confirmed what Symantec and others have reported. Cornelius’ then moved onto how difficult it is to remove the worm from a system once it has a foothold. The number of different migration techniques available to the worm means that it quickly spreads to new machines in a control system in ways that are surprising to all researchers. The Diagram shown here highlights the Multiple Pathways for Stuxnet Infection. |
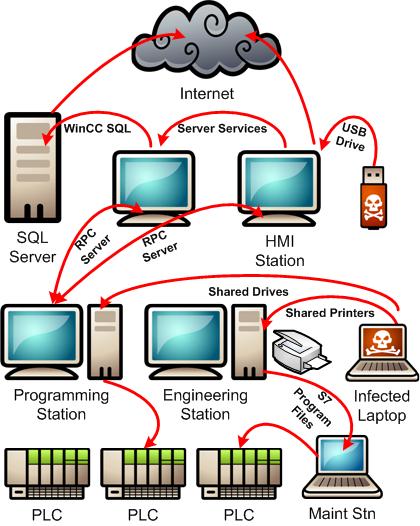 |
“Forget about the Siemens part of this”
A common theme with all the speakers, including Cornelius, was that this isn’t just a Siemens problem. Walter Sikora of Industrial Defender said it well: “Forget about the Siemens part of this – the framework can be reused for any control system”.
The structure of the worm indicates that it is a framework for attacks, rather than a one-shot tool. It probably wasn’t supposed to be discovered, but now that it has been, others will reuse it for their own purposes – probably ones that are focused on systems other than Siemens.
“The USB drive is not the villain.”
Neither Cornelius nor any of the other speakers went after the USB drive as the villain. They all know that while this time it might be a USB drive, the next time it could be a contractor’s laptop, a remote support VPN or even a serial line that is the starting point for infection.
Instead, Cornelius and other speakers made improved network segmentation (aka dividing the network into zones) their top priority for control system end-users. “No more flat networks” said Cornelius. “Control systems need lots of Functional DMZs (demilitarized zones)”.
But what exactly does “No flat networks” mean?
“No flat networks” means avoiding a network design where communications are free to flow throughout the control network. Security experts generally agree that segmenting a control system network into security zones is the most effective way to prevent the rapid spreading of malware (or other network problems such as traffic overloads).
In fact industry standards such as ANSI/ISA-99.02.01 and IEC-63443 recommend zone-based network segmentation. With zones, if an infection such as Stuxnet does accidentally occur, it is limited to a small number of machines in a single zone.
What are "security zones"?
A security zone is a group of assets that share common security requirements based on factors such as control function, operational requirements and criticality. A simple solution is to implement core zones such as:
- Safety Integrated System (SIS) zone,
- Basic Control / PLC zone,
- Supervisory / HMI zone,
- Process Information / Data Historian zone
- IT Networking zone
For additional security and reliability, each of these primary zones should be further divided into sub-zones, based on operational function. Increasing the number of zones progressively restricts the spread of a worm like Stuxnet to fewer computers, reducing both risk and clean-up costs if an infection were to occur.
I am going to connect the concept of “security zones” with real-world solutions in my next blog post.
In the meantime, if you want more information on zone level security, see the presentation below. It was created before Stuxnet, but the information about ANSI /ISA-99 and security zones may be just what you need.
![]() "Building Intrinsically Secure Control and Safety Systems Using ANSI / ISA-99 Security Standards for Improved Security and Reliability - Presentation"
"Building Intrinsically Secure Control and Safety Systems Using ANSI / ISA-99 Security Standards for Improved Security and Reliability - Presentation"


Comments
Separation Paradigm
This is an important step forward Eric. Conceptually this is simply domain separation, but the term does not seem to get much use in infosec.
One of the things we do is multiple domain separation (US DoD verified) where we use algebraic modelling to create zones in existing flat networks. (closed zones)
The other thing to think about is the interface of such zones and how can high assurance systems secure the gateways.
Add new comment