SCADA Security: Justifying the Investment
|
In my blog article Industrial Data Compromise – The New Business Risk I recommended that End Users and Control Engineers need to redouble their efforts in relation to securing their process. However, finding the best way to justify the costs of implementing and maintaining a more secure process environment is new territory even for the most seasoned control system engineer. In this article I suggest a way to determine the right amount of investment in ICS and SCADA security measures. |
 |
The Challenges Facing Control Engineers Today
Industrial control engineers are finding added complexity invading their world at an accelerated pace. Global competition continues to drive expectations of increased productivity. New technologies with shorter device life cycles demand compressed “pilot” project testing time. And the networking of everything forces tight integration between the enterprise network and the previously isolated, fit-for-purpose, process control network (PCN).
More and more, standardized technologies such as the Microsoft® Windows operating system and Ethernet TCP/IP allow PCNs to migrate to open systems. Connecting control devices to such networks exposes their latent vulnerabilities to cyber attack. The result is increased production, safety and revenue risks to plant operations.
Reducing operational costs while reliably improving up-time (productivity) through effective use of new technology remains a daunting task for today’s control system engineer. Underpinning this challenge is tighter scrutiny from a more vigilant corporate financial officer (CFO) seeking stronger justification for the costs attached to the deployment of these same technologies.
Security Risks Can No Longer be Ignored
In a post-Stuxnet world, it is clear that automation devices present a target-rich environment for cyber attacks. Control devices are part of industrial networks typically connected directly to major infrastructures such as pipelines, electrical grids, and process equipment. The exposure these devices present to a cyber attack is huge.
Most informed people believe it’s not a matter of if, but when the attack will occur. And the outcome of an attack may result in the loss of proprietary or confidential information, damage to equipment, and, if severe enough, loss of public confidence in the company.
|
How much of a chance are you willing to take on your firm’s reputation? A reputation, perhaps built over years, can easily be laid to waste in a single “event”. Let’s assume you realize that you can’t ignore the risks of security incidents, but you don’t have an unlimited budget to apply to security measures. Too much security would burden your organization unnecessarily, while not enough can significantly harm it. Striking the right balance is key. |
 |
Risk Assessment is the First Step
How do you place value on the right amount of investment that fits your security requirements? You may want to start by figuring out how much is needed to mitigate the risks or to reduce the residual risk to an acceptable value for the business.
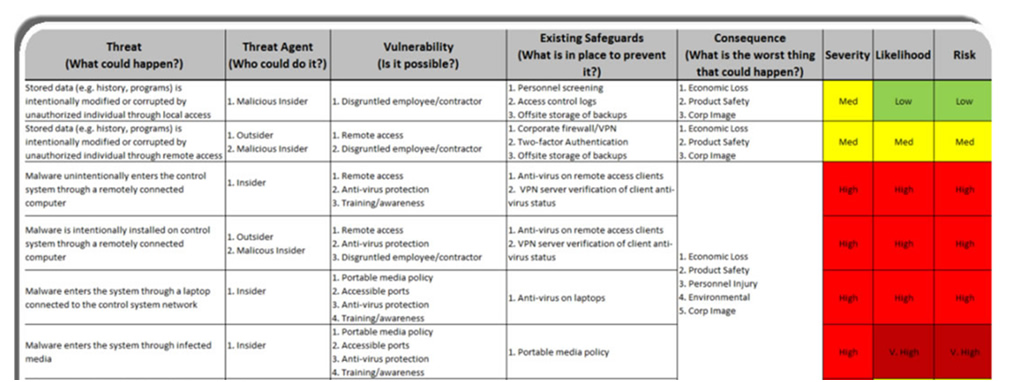
Step 1 of our white paper “The 7 Steps to ICS and SCADA Security” explains how to do a Risk Assessment and provides an example of a high-level ICS risk assessment. Each threat and its potential consequence are identified, and the Severity, Likelihood and Risk of the consequence are rated using a High, Medium or Low scale. Doing a Risk Assessment gives you the information you need to prioritize your security efforts. Now, how do you decide how much to spend to prevent or mitigate threats?
Example of a High-Level ICS Risk Assessment, from the white Paper “The 7 Steps to ICS and SCADA Security”
ROI calculations don’t provide a true measure of the costs associated with security measures. In fact, there is no return in the traditional sense unless there is an event. And then the return is priceless!
So, how does an alert Control Engineer justify the costs to management? Many are using a comprehensive approach that includes the Risk Assessment component discussed above, along with a Total Cost of Ownership (TCO) financial calculation.
Next Calculate the Total Cost of Ownership of Security Measures
In simple terms there are two types of costs: direct costs and indirect costs. Direct costs are easy to define and consist of the actual purchase price of the security hardware, software and/or services. This may also include having a third-party with expertise in control system security do the Risk Assessment, particularly if it is a first time exercise for your organization.
Indirect costs are a bit trickier. Often times, these costs tend to dwarf the amounts related to direct costs and are more difficult to define, quantify and capture. Staff costs are usually the biggest component here, and they include costs related to training, installation, monitoring and upgrading security technologies.
In today’s security environment TCO also includes the potential lost value from not putting security measures in place. These ‘hidden’ indirect costs include loss of operational productivity as well as the time lost by Control Engineering and IT staffers responding to malware.
Determining the Right Amount of Investment in SCADA Security
Calculating the right amount of investment in cyber security measures is best summarized as follows:
- Estimate the potential cost of individual security incidents with the help of the threats and ratings determined in the Risk Assessment.
- Develop an annual model for security incidents and determine the total annual cost.
- Optimize your spending on security by relating the annual security TCO to the annual cost of security incidents.
You do not need to become an expert on risk calculation or a financial genius to do this analysis. The important thing is that your spending on SCADA security is the result of a quantifiable analysis and not merely a subjective figure.
According to a 2010 survey of over 1500 companies with mission critical applications conducted by Gartner Technology Research Group, the average manufacturing organization is spending about 5% of its manufacturing IT budget on security.
Companies should not necessarily worry if spending is higher or lower than the average noted in the survey, rather each firm must decide if their security spending is at the level that provides adequate mitigation and risk reduction to potential threats.
That’s my opinion, what’s yours?
Related Content to Download
|
White Paper - "7 Steps to ICS and SCADA Security" |


Add new comment