Making Security Simple with the Next Generation Tofino Cyber Security Solution
When I started Tofino Security in 2006, my two goals were to make industrial cyber security easy to deploy and better suited for the real needs of mission critical networks. Our first generation products went a long way in doing that, but like any initial offerings they reflected a limited feedback loop from users in the field.
Today I am proud to say that we have integrated lessons learned over the last eight years to deliver Tofino 2.0, our next generation of industrial cyber security solutions.
Tofino 2.0 is a suite of products and services that includes:
- A new set of security appliances—the Tofino Xenon product line
- A new software tool—the Tofino Configurator 2.0
- A new Deep Packet Inspection Loadable Security Module (LSM)—the Tofino EtherNet/IP Enforcer
All products are now integrated with online licensing systems, plus made-to-order manufacturing. I believe this combination makes it extremely easy for control systems professionals to deploy ready-to-go cyber security solutions that work.
While normally my articles are designed to help educate you on industrial security topics, I hope my enthusiasm for Tofino 2.0 will convince you to read further and find out how this new generation makes implementing security on the plant floor both flexible and simple.

Introducing our new Tofino Xenon family of state-of-the-art security appliances
The Tofino Xenon Security Appliance: Maximum Data Security for Harsh Environments
To start, we have a whole new hardware platform. The Tofino Xenon is a security appliance with new state-of-the-art hardware that is made to order for each environment or industry. When ordering the hardware, the security engineer can specify exactly what they need to get the job done and have it made-to-order by the Belden factory.
For example, Tofino Xenon is designed to support three different temperature operating ranges. This lets you pay only for what you need:
- If you are putting the Tofino Xenon in a rack room, specify the 0° to 60°C version and save yourself some money.
- Do you need it for a pulp mill with high temperatures and corrosive gases? Then order the Tofino Xenon -40° to +70°C version with Conformal Coating.
Check out all the current hardware options in the on-line Product Configurator.
The Tofino Xenon appliance now comes pre-loaded with our proven stateful Firewall and Event Logger LSMs. The Firewall LSM filters Ethernet-based protocols at layers 2, 3, and 4 of the OSI model. As always, it can be deployed into live networks without risk of disruption, without requiring network changes, and without pre-configuration. It is ideal for segmenting a control network into security zones.
The completely updated Event Logger LSM offers simultaneous logging to remote syslog servers and non-volatile local storage of over 1 million events.
Ready to Go Out of the Box
Another area where we have made improvements is in the installation and commissioning process. With the previous generation of Tofinos, the Deep Packet Inspection (DPI) LSMs had to be downloaded from our licensing system and installed in the appliance.
Now you can order the Tofino Xenon with all the DPI LSMs loaded and licensed at the factory. Of course, our flexible licensing feature didn’t go away – if you decide you need another LSM after you have your Xenon, you can order and upgrade your appliance online.
Once you have your Tofino Xenon in your hand, it is ready to go. As always, the Tofino can be installed without risk to operations. The moment it is powered up, the Tofino Xenon is activated in “Test” mode, where it listens and records traffic, but doesn’t block anything.
This way there are no process upsets because of incorrect rules. In fact, if you want a quick and easy traffic recording system, you can stop right there and never configure a single rule. But I suggest you don’t do that – the new configuration tool is too cool to miss.
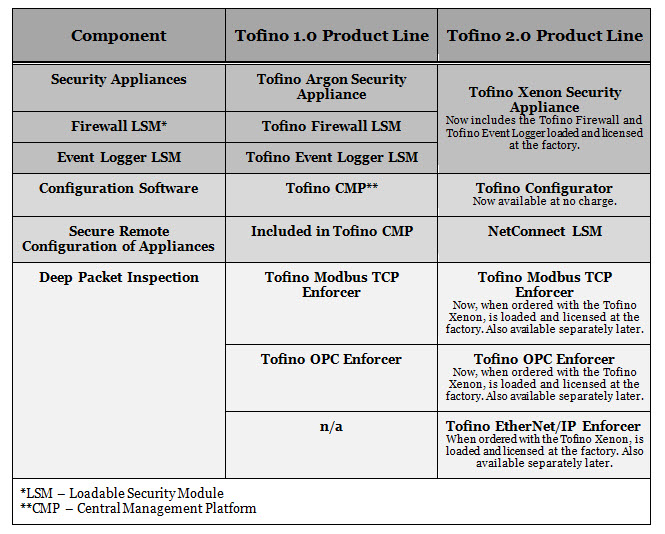
Chart Comparing Tofino 1.0 and 2.0 Product Lines
The Tofino Configurator 2.0: Simplicity for Novices/Flexibility for Experts
One of the things we learned with our first generation products was that configuration of the security devices needed to be simpler for those just beginning to manage network security. Yet Tofino also had to offer detailed options for advanced users. We have solved this by providing a new no-charge Windows-based management application called the Tofino Configurator 2.0 (TC 2.0).
The first thing you will notice about TC 2.0 is that it is based on the look and feel of Windows Explorer. We did this because no matter what you think about Windows® as an operating system, everyone in the world knows how to use the GUI (Graphical User Interface).
The Tofino Configurator 2.0 comes with hundreds of pre-defined templates for all of the popular makes and models of industrial controllers. For those new to ICS security, these templates define common “Rule Profiles” that specify the protocols that a given control device typically supports, along with how those protocols are best managed.
For example, a template might specify that a certain PLC always uses the Modbus protocol as a slave (i.e., the PLC responds to requests from HMI masters). The profile may also include rules to block packets that could exploit known vulnerabilities or rate limits if the PLC is susceptible to DoS attacks. The Firewall Rule Wizard then uses this information to automatically create appropriate rules for the PLC.
Advanced users can always manually create and tune their own rules, but we suggest they create templates tailored to the company policies and share those with their fellow engineers. For example, a security expert could create a “View-Only HMI” template for Modbus or EtherNet/IP that, when used, would result in the Tofino Xenon blocking all ICS messages that do not contain read commands.
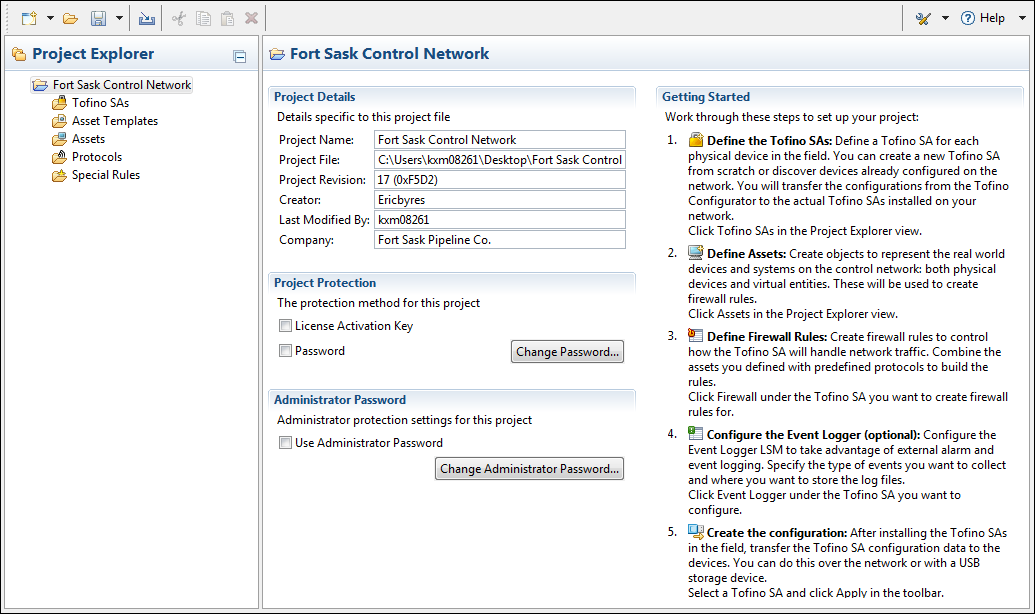
The New TC 2.0 is immediately familiar to anyone who has ever used a Windows PC.
The Tofino EtherNet/IP Enforcer: Deep Packet Inspection for Rockwell and ODVA Protocols
The stateful firewall that comes with the Tofino Xenon Security Appliance is a proven and excellent firewall. However, as I hinted above, to protect the “crown jewels” of your operation, I recommend using Deep Packet Inspection (DPI) technology.
DPI technology understands specific ICS protocols and applies the appropriate filters to enforce proper security policies. As in my earlier example, it can enforce security policy such as allowing only read commands to be sent to a PLC and blocking all potentially dangerous commands.
Until now we have provided DPI LSMs for OPC Classic (Tofino OPC Enforcer LSM) and for Modbus/TCP (Tofino Modbus TCP Enforcer LSM). With the addition of the EtherNet/IP Enforcer LSM, we are now offering advanced security for another popular protocol.
EtherNet/IP is a protocol that pushes Tofino’s vision of simplicity with flexibility to the limits. Arguably one of the most complex ICS protocols in the world, few controls professionals truly understand what the traffic on the wire really looks like.
Ask an engineer what CIP services they want to block to create a read-only PLC and I will bet that 99.99% can’t tell you. Many could not even tell you what CIP services are*. And it is for good reason: the CIP services are very complex and those that can write to a PLC vary from object to object. Many are undocumented and some act as both read and write functions. If you want to see just how challenging EtherNet/IP and CIP are to secure, check out our academic paper presented at this year’s ODVA conference: “Securing EtherNet/IP Control Systems using DPI”.
In order to address this challenge, the Tofino team created an abstraction layer called CIP Service Groups. This allows control professionals that are new to EtherNet/IP security to simply select a general description of the operations their device should be performing using EtherNet/IP. The Tofino Xenon then makes the decision as to the correct CIP object and service combinations to be allowed to meet this objective.
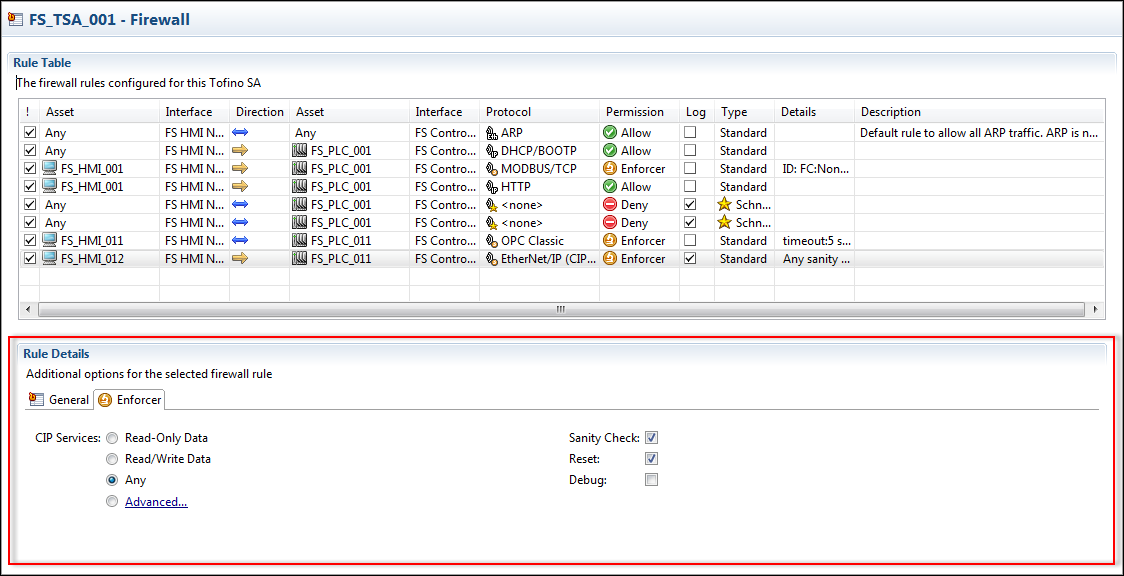
With the Tofino EtherNet/IP Enforcer, an optimized rule is created with a simple click of the Read-Only Data button.
For the expert user there is an Advanced dialog box that allows them to identify the CIP objects that their control system uses and then select the CIP services that they want allowed on those objects.
In summary, the unique Tofino EtherNet/IP Enforcer makes securing a complex industrial protocol straight forward for both controls professionals and security experts.
Imagining Security Simplicity
The team at Tofino Security has learned a lot about making security simpler and better over the past eight years of product development. We have also gained invaluable experience from thousands of Tofino installations.
But most of all we have learned from all of our friends, clients, and critics who have told us what has worked in their plants, refineries, and substations. These same people have not shied away from telling us when we messed up and we have strived to address those concerns with the 2.0 product line.
I believe that the new Tofino 2.0 release captures the best of what we learned to create the easiest to use, most flexible, and most secure industrial security product on the market. Check out a demo of the new Tofino 2.0 and let me know what you think.
(To arrange for a demo, contact your Belden account manager or call 1-855-400-9071, option 2. Alternatively, email us at www.belden.com/contact.)
*CIP stands for Common Industrial Protocol, an application layer protocol defined by the Open DeviceNet Vendors Association (ODVA). CIP is the top layer protocol in EtherNet/IP communications, sitting on top on other well known protocols like Ethernet and TCP/IP. The ODVA defines a CIP service as “A function supported by an object and/or object class”. Think of CIP services as a set of predefined actions that a client device (such as an HMI) can request a server device (such as a PLC) to perform on one or more CIP objects (such as a digital input object). Still confused? Check out the ODVA white paper “Common Industrial Protocol (CIP™) and the Family of CIP Networks”.
Related Content to Download
|
Technical Briefing Kit - "Understanding Deep Packet Inspection for SCADA Security"
|
Related Links
- Press Release: “Belden Introduces Its Next Generation of Industrial Security Solutions”
- Webpage: Tofino Xenon Security Appliance
- Belden e-Catalog Webpage: Tofino Xenon Security Appliance Product Configurator
- Webpage: Tofino Configurator
- Webpage: Tofino EtherNet/IP Enforcer
- Academic White Paper (Tofinosecurity.com site registration required for download): Securing EtherNet/IP Control Systems using DPI
- Webpage: Tofino Legacy Products and Support


Comments
Eval equipment
I lead the security team at a large consulting firm in Calgary- we have many energy clients and I'd like to better understand your product line to see if it's a fit in our move to operational tech security. Do you have any demo lab gear we could evaluate?
Thanks,
Chris
Add new comment