Upgrading Windows XP – Mitigate the Vulnerabilities Immediately Using an Industrial Firewall – Part 2
Author Mike Miclot
On the eve of April 8, Microsoft retired support for the Windows XP operating system (OS) – leaving millions of Windows XP users susceptible to accidental and deliberate security issues. Though the retirement had been long planned and with fair warning, industrial network users are just beginning to comprehend the ramifications.
And it’s not that Windows XP will no longer work – it’s that Microsoft will no longer provide patches, security updates or infrastructure support, leaving industrial networks vulnerable to production disruptions and system downtime.
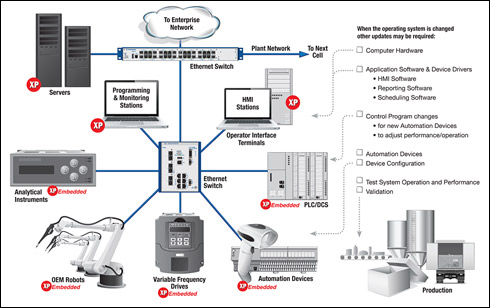
Even more concerning? Windows XP is the most popular OS for industrial users. It can be found in ruggedized PCs performing mission-critical tasks, such as control, safety and asset management, as well as embedded in thousands of devices used in factory automation and process control operations.
Those responsible for protecting critical industrial processes and networks are left with few options. And a system upgrade isn’t as simple as it may seem – one upgrade can trigger a lengthy "domino effect."
Upgrading to a new operating system triggers a domino effect of new hardware and equipment purchases, new driver installations, system integration work, testing, training and lost operational productivity.
What is the "Domino Effect?"
Ultimately, upgrading to a new version of Windows will be necessary, but it’s not a quick project.
An upgrade will come with a long list of strings attached. It means migrating from an operating system that includes a variety of applications, hardware and software programs. And upgrading isn’t a one size fits all solution – it requires time, hefty costs, and risk associated with network downtime and operational productivity.
The "domino effect" triggered by an OS upgrade involves a number of steps, including:
- Upgrading the operating system
- Purchasing and installing:
- New PC hardware and/or automation devices
- New software for the new equipment
- New communication drivers for the new software
- Ensuring automation devices work with the new software and drivers
- Conducting system integration work (since the mission-critical applications on your network may behave differently)
- Deploying modified applications
- Performing extensive testing on the new systems
- Executing user training and support for the new systems
Now, imagine completing that process for every Windows XP install you have, and you can see how a “simple” OS upgrade can take several man years of effort.
To upgrade just 1 computer running Windows XP to a new OS necessitates many other updates that then require testing and validation before being put into operation.
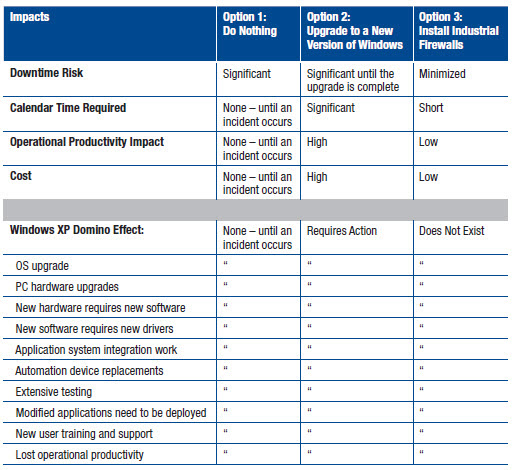
Update on Your Own Schedule: Enforce Industrial Firewalls
Not everyone is ready to change the way they operate. For those who prefer to continue running on Windows XP – and tackle the upgrade of their OS on their own time – employing industrial firewalls is an immediate solution for protecting Windows XP-based systems.
Applying industrial firewalls to your network:
- Is a simple installation that can be configured quickly
- Requires minimal staff time, training and support requirements
- Does not involve upgrading or replacing other systems and is designed for all industrial environments
- Is cost effective
- Provides the option to create your own timeline for migrating away from Windows XP
There is no "domino effect" for enforcing industrial firewalls – essentially offering immediate peace-of-mind while securing your network from potential security incidents – from internal accidents to cyberattacks.
A comparison of options for securing industrial applications after the Windows XP EOS.
What are your thoughts on the best way to deal with the EOS for Windows XP? I look forward to hearing from you.
Related Content to Download
Related Links
- Press Release: Belden Helps Secure Industrial Applications With the End of Windows XP Support
- Microsoft Webpage: "Windows XP support has ended"
- Webpage: Security Capabilities
- Blog: How the the Windows XP End of Support will Impact Industrial Applications - Part 1
- Blog: SCADA Security Basics: Why Industrial Networks are Different than IT Networks
- Blog: ICS Security: How Your IT Dept. Can Help
- Blog: Industrial Networking: Easy Security Risk Assessment
![]() Subscribe to the "Practical SCADA Security" news feed
Subscribe to the "Practical SCADA Security" news feed
Microsoft and Windows are registered trademarks of Microsoft Corporation in the United States and other countries.



Comments
More?
Can you say more about how an industrial firewall protects these Windows XP systems that are now unpatched?
How an industrial firewall helps protect unpatched systems
Add new comment