Stuxnet and DoS Attacks on SCADA News Lists means Increased Risk for Industrial Control Systems
Thanks to all the publicity around Stuxnet, there has also been growing interest regarding the reported Denial of Service (DoS) attacks against the industry mail list that I sponsor, SCADAPerspective. I want to take this opportunity to set the record straight on what actually happened back in July 2010 and to let you know why it signifies increased risk for all industrial control systems.
Analysis of DoS Attacks on SCADAPerspective and SCADASec News Lists
The attacks occurred on July 16th, the same day that the larger SCADA community first started becoming aware of the Stuxnet worm. And, for reasons explained below, the attacks may be related to Stuxnet.
Using reports that were salvaged from SCADA Perspective’s Internet Service Provider (ISP), the DoS attack started the moment that messages regarding Stuxnet malware began to be delivered to valid list recipients.
I later learnt that another mail list dedicated to supporting the industry, SCADASECL, was also affected in a similar way. After comparing notes on the outage with the other list administrator, Mr. Bob Radvanovsky, we realized that the following observations were common to the attacks on both systems:
- The attacks on the SCADASECL & SCADA mail list server systems occurred around the same moment and were of the same duration.
- The sources of the attacks were from a Chinese domain address range. Of course this does not mean that attackers were Chinese, just that the traffic was emanating from that IP address range and could easily be controlled from another country.
- The attacks comprised of a combination of ICMP Type 0 (network unreachable) and ICMP Type 3 (port unreachable) errors, along with brute force root login (rlogin) attacks.
- The brute force root login attacks on the SCADASECL & SCADA mail list server systems were from two IP-addresses from the same subnet range originating from a Chinese domain.
The outcomes of the attacks were:
- The domain controller resolving SCADAPERSPECTIVE.COM suffered such excessive traffic that there was an outage of the mail server.
- The SCADASECL list fared much better - while network performance was impacted, no system outages resulted. (This is not bad for a guy with a server farm in his basement and gear held together on a shoestring budget. All to provide a service to the community for free.)
Unusual activity on SCADAPerspective has occurred before
While this is the first time I have seen a successful DoS attack on SCADAPerspective’s mail list system, it is not the first time it has seen some curious activity.
For example, interest in its web facing server pages peaked at the same time as scanning for SCADA centric ports spiked - soon after the public disclosures of SCADA specific vulnerabilities.
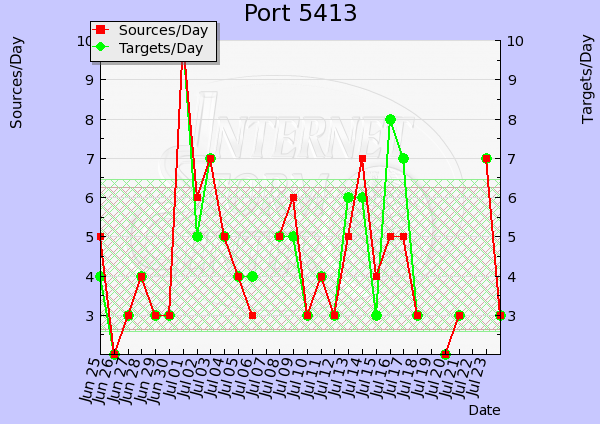
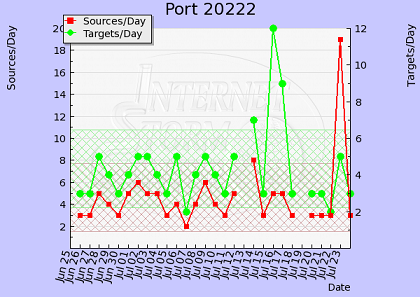
Most notably this occurred when the Wonderware and Citect vulnerability disclosures were posted on the US-CERT vulnerability database. What occurred was a marked increase in search phrase and word requests from IP addresses with North Korea, China, Romania, and Russia country domains.
These domains downloaded more data over each case and period of time than the usual highest download domain, the USA. What was most notable was that the timing of the activity was closely tied with the subsequent peak alerts of the ports identified in each vulnerability’s disclosure report (data source: SANS storm centre traffic analysis).
Additionally, I am aware of reports in the media* of there being something in the order of approximately a fourfold increase of attacks from Australia and a two and a half fold increase in targeted activity directed towards the Australian military, in the last twelve months.
Implications for Critical Infrastructure Operators
So what does this mean to us as a community? To me these observations clearly demonstrate that SCADA or Industrial Control Systems are certainly a hot topic of interest to hackers, if nothing else.
Going further than that, I am of the firm opinion that the increase in number of vulnerability disclosures to the public is a significant indicator for our community to note. We must recognize that these developments profoundly change the base level of cyber risk for every industrial control system.
In my opinion, every owner or operator of critical infrastructure that is of local, national or global interest, wherever you are located, needs to pay attention to the new higher risk of cyber attacks. You need to counter this risk by:
- Implementing best practices mitigation techniques, policies, and procedures for your system design.
- Investing sufficient people and financial resources to enable 1.
- Testing and validating your preparedness regimes.
Bottom line – after the developments described here, can you afford to proceed with an unchanged risk appetite? What do you need to do to guarantee that your enterprise is resilient now and in the future?
* The Sydney Morning Herald, Oct 9, 2010: Military faces huge cyber threat
The Sydney Morning Herald, Sept 19, 2010: Cyber Storm about to unleash chaos on Australia, the world
This article is a special guest contribution by:

Ron Southworth |
Practical SCADA Security thanks Ron for this article.


Add new comment