The NIST Cybersecurity Framework - What is it and what does it mean to you?
You may have heard some buzz in the press (both US and International) about the release of the Cybersecurity Framework Draft from the US National Institute of Standards and Technology (NIST). However, you may not know much about its background. And you probably don’t know what it may mean to you as a control or security professional. This blog post will give you a high level overview of the genesis of this document and some handy points of reference.
The Executive Order That Gets It all Rollin’
Regardless of where one lives in the world, we all know that our country’s national infrastructures are very important to our economies and our national defense. And with incidents like the attacks on the gas pipeline industry and the details revealed in the Madiant Report, nowhere has this point been driven home more than in the US.
So due to the growing concerns over continued cyber attacks on US national infrastructure – such as the electric grid, water systems, transportation networks, banks/financial institutions, critical manufacturing, etc. – President Obama issued Executive Order 13636, "Improving Critical Infrastructure Cybersecurity," on February 12, 2013. This document is fondly referred to as the "EO."
Executive Order on Cybersecurity: A Sign of the Times? Image Credit: Mashable
The EO called for development of a voluntary Cybersecurity Framework to provide a "prioritized, flexible, repeatable, performance-based, and cost-effective approach" for assisting organizations responsible for critical infrastructure services to thus manage cybersecurity risk.
Critical infrastructure is defined in the EO as "systems and assets – whether physical or virtual – so vital to the US that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters." Example industry sectors and the corresponding Federal oversight agency in the US that are considered as "critical infrastructure" are shown in the table below.
| Sector | Federal Oversight Agency |
|---|---|
| Chemical | Department of Homeland Security (DHS) |
| Commercial Facilities | DHS |
| Communications | DHS |
| Critical Manufacturing | DHS |
| Dams | DHS |
| Defense Industrial Base | US Department of Defence (DOD) |
| Emergency Services | DHS |
| Energy | US Department of Energy (DOE) |
| Financial Services | US Department of the Treasury |
| Food and Agriculture | US Department of Agriculture US Department of Health and Human Services (HHS) |
| Government Facilities | DHS and US General Services Administration (GSA) |
| Healthcare and Public Health | HHS |
| Information Technology | DHS |
| Nuclear Reactors, Materials and Waste | DHS |
| Transportation Systems | DHS and US Department of Transportation (DOT) |
| Water and Wastewater Systems | US Environmental Protection Agency (EPA) |
Designated Critical Infrastructure Sectors and Sector-Specific Agencies in the US1
As a follow up to the EO, NIST was assigned responsibility for development of the Framework in collaboration with industry feedback. The Framework is intended to provide guidance to an organization on managing cybersecurity risk. A key objective of the Framework is to encourage organizations to consider cyber security risk as a priority similar to financial, safety and operational risk, while factoring in larger systemic risks inherent to critical infrastructure.
The previous sentence is important – if the framework is accepted, then cybersecurity risk and considerations need to be included in the day-to-day discussions at your company or organization. As you expand your business, build new facilities, install new equipment and hire new people, cyber security must be part of the management discussion.
Okay – Now Let’s Talk About the Framework
First, the EO instructed NIST to be the lead in developing the Framework. They did and now you can find the Framework DRAFT document (and supporting information) at www.nist.gov.
So what does the Framework contain? According to the Cybersecurity Framework Overview, the Framework shall:
- include a set of standards, methodologies, procedures, and processes that align policy, business, and technological approaches to address cyber risks.
- shall incorporate voluntary consensus standards and industry best practices to the fullest extent possible.
- shall be consistent with voluntary international standards when such international standards will advance the objectives of this order. And, what is the Framework supposed to do?
Again according to the overview documents, the Framework:
- shall provide a prioritized, flexible, repeatable, performance-based, and cost-effective approach, including information security measures and controls, to help owners and operators of critical infrastructure identify, assess, and manage cyber risk.
- shall focus on identifying cross-sector security standards and guidelines applicable to critical infrastructure.
- will also identify areas for improvement that should be addressed through future collaboration with particular sectors and standards-developing organizations.
- should provide guidance that is technology neutral and enables critical infrastructure sectors to benefit from a competitive market for products and services that meet the standards, methodologies, procedures and processed developed to address cyber risks. And,
- shall include guidance for measuring the performance of an entity in implementing the Cybersecurity Framework.
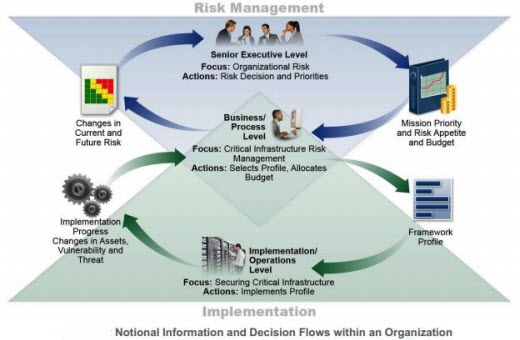
NIST’s model of security information and decision flows within an organization (Source: NIST Preliminary-Cybersecurity Framework, Page 9)
So, with the guidance above – and with input from industry – the draft of the Framework is intended to provide a common language and mechanism for organizations to:
- Describe their current cybersecurity posture (and a semblance of maturity level)
- Describe their target state for cybersecurity
- Identify and prioritize opportunities for cybersecurity improvement within the context of risk management
- Assess progress toward the target state, and
- Foster communications among internal and external stakeholders.
A key aspect of the Framework is that it is not intended to replace an organization’s existing business or cybersecurity risk management process and cybersecurity program. Instead, the organization can use its current processes and leverage the Framework to identify areas to improve its cybersecurity risk management. Also, the Framework can be helpful to a company that does not have a currently existing cybersecurity program so they can build in key elements raised by the Framework.
What Should You Do with the Framework?
First of all, take a look at the list of the critical infrastructures listed above. Does your company fall into any of those categories? If not, is your company substantially reliant on any of those key infrastructures for your success and even existence? If the answer to either is YES then I’d suggest you take time to read the draft Framework as it stands and figure out how you can apply it to your current cybersecurity risk management.
Secondly, acquaint your Executive Management and Board Members with the Framework. Give them a sense of how your company stands today relative to the Framework Implementation Tiers listed. Use this as a means of highlighting your organization’s "Cybersecurity maturity level". If you aren’t near the top, use it to highlight the resources (i.e., people, time and money) you need to raise your game.
Thirdly, take a hard look at the Framework and "test drive" it as it stands. Then provide comments back to NIST as described at their page "Request for Comments on the Preliminary Cybersecurity Framework." Comments must be submitted before December 13, 2013, so you don’t have much time.
Final Thoughts
When you read the draft Framework, recognize that it is not a “checklist” or a simple “compliance” item to be fulfilled. Nor is it a “how-to” on building a security program (check out ISA/IEC-62443.02.01 for that). Instead the framework provides a set of performance objectives for your cybersecurity risk program to achieve against your prioritized list of key assets.
So consider the framework to be a nationwide score card for security preparedness. Maybe even an international score card. Either way, you don’t want to be at the bottom of the class with the hackers come calling.
Tofino Security thanks Ernie Hayden for this article.
Related Content to Download
|
Presentation - "ICS Security - What's happening and what are the challenges?" |
Related Links
- Webpage: Executive Order - Improving Critical Infrastructure Cybersecurity
- Webpage: Presidential Policy Directive - Critical Infrastructure Security and Resilience
- NIST Presentation: Cybersecurity Framework Overview
- Improving Critical nfrastructure Cybersecurity Executive Order 13636
- Blog: Cyber Attacks on U.S. Critical Infrastructure will Intensify
- Blog: SCADA Cyber Security: An International Issue



Comments
UK perspective.
It’s interesting how governments across the world are now investing in approaches to help organisations assess and improve their cyber security posture.
Today, the UK Department of Business Innovation and Skills (BIS) have announced their approach to organisational cyber security. The approach is different to the NIST framework.
In my simplistic view, BIS is essentially going to define a profile of ISO 27001 (in an ambitious time frame). The profile will say “These are the really important bits, you really must do as a minimum” and “If unsure how to do them, here is a pattern of what good practice looks like”. Organisations will be able to adopt this as a model to improve their security and then, if appropriate to their business, seek validation from an external party that the controls are suitably in place.
More on the BIS approach can be found here:
https://www.gov.uk/government/consultations/cyber-security-organisationa...
Together with my views:
http://cybermatters.info/2013/11/28/reaction-to-bis-cyber-security-stand...
Reply to BIS Approach Discussion
Thanks, Mr. Robbins, for your comments. Much appreciated!
During the initial development of the NIST Cybersecurity Framework there were concerns that the NIST format would simply collect all the available cybersecurity standards in the US then essentially reformat them into the Framework.
Fortunately, that was not the case. Instead they have gone more to a performance-based approach that includes performance objectives and criteria...rather than specific compliance "minimums."
This approach is definitely more refreshing than the pure compliance approach to cyber security I've witnessed these past 4+ years in the U.S.
I hope this helps and thanks again for the links to the BIS approach.
Cheers!
Ernie Hayden CISSP CEH
The NIST Cybersecurity Framework - What is it and what does it m
Ernest, nice work in providing a summation of the framework. A good "apertif" before the main course :-)
Thanks!
Thanks, Don, for the compliments!
This information is not "rocket science" and we all need to understand the fundamentals before it pounces on us!
Cheers!
Ernie Hayden
Add new comment