Fixed Configuration Firewalls, Safety Systems and Reduced Human Error
Earlier this week Patrick Coyle wrote an excellent blog on Safety Integrated Systems (SIS) and why they are so important to safe industrial operations. If you are new to the SCADA and ICS world, or if you have mostly worked on non-safety related processes, I highly recommend you read his blog.
Now of course I also like the fact that a new firewall product released by Honeywell which is based on our Tofino Security technology got this topic rolling. But best of all, Patrick asked some questions that I never thought to answer. Important questions about what exactly Honeywell is selling and how it secures safety systems. So here goes…
The Honeywell Modbus Read-only Firewall (HMRF) is what is known as a Fixed Configuration Firewall (FCF) which runs a technology known as Deep Packet Inspection (DPI). In today’s blog I am going to explain the fixed configuration firewall part. Later this month I will tackle DPI.
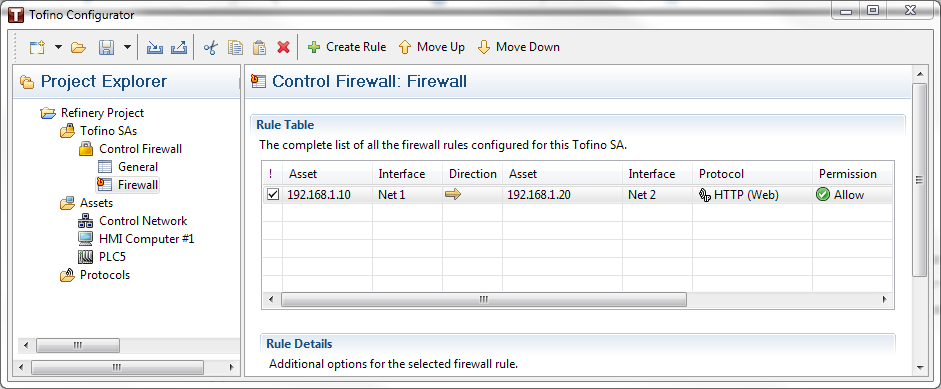
Nearly all firewalls on the market are designed to be configured to allow or block traffic using Access Control Lists (ACL). For example, if you only want to allow web traffic (i.e. HTTP traffic) from a client at IP address 192.168.1.10 to a web server with an address of 192.168.1.20 you might enter an ACL like the one in the image below.
The good news is that being able to enter ACLs gives the firewall administrator a lot of flexibility. If today the firewall is being used for managing web traffic and tomorrow database traffic needs to be allowed, it is simple to adjust the ACLs. And since flexibility is what most IT security experts want, that is what the firewall vendors like Cisco and Juniper have given them. It is also what the standard version of the Tofino firewall offers – flexibility to define multiple rules for absolutely any protocol and any IP address.
But with flexibility comes a price – increased chance of both human error and human evil.
Human error in firewall configuration
The amount of human error in firewall configuration can be staggering. For example, an IEEE paper on firewall errors showed that even critical IT firewalls in major corporations can have poorly written rule sets. In the study the author, Dr. Avishai Wool, defined 12 serious firewall configuration errors (each very general in nature) and then inspected the firewall configurations of 27 major corporations. He found an average of 7 serious errors per firewall, with some having as many as 12 errors. At that point, you might not even bother having a firewall for all the good it is doing you.
To address the human factors issue, most companies must both carefully document their ACLs and conduct regular firewall rule reviews and security audits. For example, NERC-CIP-005 (which deals with firewalls) states:
R5.1. The Responsible Entity shall ensure that all documentation required by Standard CIP-005-2 reflect current configurations and processes and shall review the documents and procedures referenced in Standard CIP-005-2 at least annually.
Now rule audits do not come cheap – often a good audit costs more than the cost of the firewall. And for that matter, even the expert labor needed to configure the firewall can be more expensive than the firewall. All this adds up to a significant Total Cost of Ownership (TCO) over the life of the firewall.
Human evil in firewall configuration
As for the human evil side, if firewalls can be configured to detect an attack they can be configured to ignore it too. All it takes is sloppy access (i.e. password) management for the firewall, so organizations like the US Nuclear Regulatory Commission ask their licensees for a lot of safe guards and audits when it comes to firewall management. Again, those cost money.
Fixed Configuration Firewalls reduce that high TCO by being locked to a single (exhaustingly tested) configuration at the factory. For example, the Honeywell Modbus Read-only Firewall is locked to only allow Modbus read commands through. All other traffic is blocked; a setting that simply cannot be tampered with.
Of course a firewall like this would not work for the normal IT space, as there are too many Adds/Moves/Changes of both applications and users. But in the ICS/SCADA space, the basic network design can stay steady state for decades. For example, if an SIS is using Modbus TCP today for communications to the DCS, it probably will be using the protocol ten years from now. In fact, if your SIS starts trying to use the HTTP protocol to connect to a World Cup Soccer site in Malaysia, you probably have a problem - a problem so big that you don’t want staff to be able to make the alarms disappear by changing a few rules.
Fixed configuration firewalls – reduced human error and human evil
By using a fixed configuration firewall, there is limited ongoing review or maintenance required. After all, if no one can ever change the rules, you don’t really need that quarterly rule review/audit. And if there is no user access to the unit at all, the issues of password management and access logging disappear.
Typically the only audit needed is to confirm the unit is in place and powered on. Occasionally some companies will run a periodic scan against the firewall, but the result of that is so black and white, it is a trivial and cheap test. Best of all, the firewall is tamper proof, so that the next Stuxnet can’t steal a password, reprogram the ACLs and sneak into your control system.
So if you have SCADA or control systems that have very consistent network traffic patterns, a fixed configuration firewall is worth considering. It can reduce the TCO of security significantly and it is a tamper proof security solution.
If you have ideas for systems besides SIS that would benefit from this sort of technology, please let me know.


Add new comment