Easy-to-use Schneider ConneXium Tofino Firewall Advances SCADA Security
One of the major differences between industrial networks and enterprise networks is that industrial networks are typically managed by engineers or technicians. Now engineers are experts at making good product, designing control loops and so on, but they are not IT security wizards. That's the reality, and it means that security products that "just work" reliably and safely with automation systems are going to be more effective in actually delivering security than products that don't.
That's why Schneider Electric is to be commended for all the measures they are taking to improve cyber security for their customers. This includes conducting a detailed security analysis of all of their major automation products and partnering with us to create the ConneXium Tofino Firewall in 2012. A new version of this product has just been released, which adds the Tofino Enforcer's Deep Packet Inspection technology for the EtherNet/IP protocol.
Let's take a look at what this product does and how its ease of use helps improve SCADA security.
Schneider Electric oil and gas automation systems can be secured with the ConneXium Tofino Firewall. Credit: arbyreed
Securing Networks from Traffic Storms, Cyber Threats and Programming Errors
In case you didn't know, ConneXium is Schneider Electric's line of network infrastructure products that interoperate with their automation products. The ConneXium Tofino Firewall inspects and secures network traffic to and from the automation devices, providing protection from traffic storms, malformed messages and deliberate hacking attempts.
In addition, it can be used to enforce plant procedure. For example, it can block inappropriate modification or programming of critical devices and controllers, preventing costly mistakes and improving overall network uptime and reliability.
Plug-n-Protect Deployment and Configuration
The ConneXium Tofino Firewall consists of a security device (hardware), a software module for configuring the devices, and software modules for securing communications.
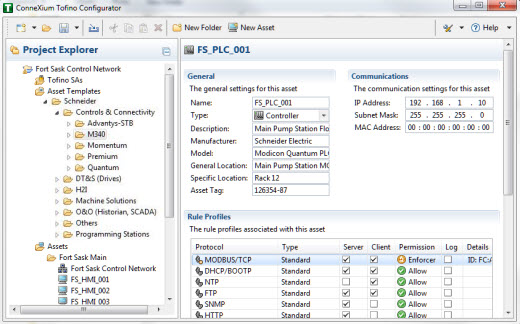
When an engineer configures the product, the first thing they see is an interface that anyone with basic Windows 7 experience will intuitively understand how to use. On the left side of the screen is a Project Explorer view. It lists the things in the facility that are important to cyber security - things like Tofino Security Appliances (Tofino SAs), Assets (e.g., PLCs, HMIs, network switches, etc.) and protocols.
Each is displayed in a tree format similar to the way that files are displayed in Windows Explorer. Any object in the Project Explorer view can be clicked to display its information in the Details view on the right had side of the screen. This is where particular values for an object can be edited.
The Tofino Configurator has a "Windows 7" interface and includes pre-configured templates for Schneider Electric automation products.
Another type of item to select from the left side is "Asset Templates". These are pre-configured templates for Schneider Electric automation products. They are designed to help define multiple assets quickly.
Rather than having to be security experts, engineers simply select the models of Schneider products they are using in their facility and create assets based on those templates. For example, if there are ten Schneider Electric M340s PLCs in the plant, the pre-existing M340 template can be used to create assets to represent all of them.
The templates really shine when firewall rules are created. Let‘s say rules are needed for communications between a Modicon PLC and an HMI. The templates include information about the protocols that the PLC is designed to use (such as Modbus), along with ways to manage the protocols.
For example, if a device like a PLC only uses a protocol as a server (i.e., it responds to requests from HMI clients), the Firewall Rule Wizard will use this information to automatically create appropriate rules to block server-like messages from going to the PLC. Template rules can be very detailed – if a PLC is at a risk from Denial of Service (DoS) attacks, traffic rate limits can be built into them.
Finally, new expert technology looks through the rules for common mistakes in firewall programming and suggests possible improvements.
Superior Protection with Tofino Enforcer Deep Packet Inspection Technology
As many of you know, most SCADA and ICS protocols do not provide granularity for the network messages. At the TCP/IP layer, a data read packet looks exactly like a PLC firmware update packet. If you allow data read packets to pass through a traditional firewall, you are also allowing the firmware update packet to pass through. This is a serious security issue.
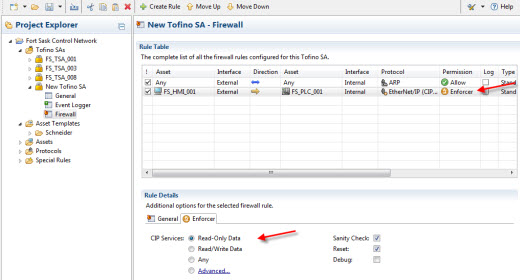
The ConneXium Tofino Firewall addressed this in its initial release with the Deep Packet Inspection for the Modbus TCP protocol. Now this has also been added for ODVA's popular EtherNet/IP protocol. The Tofino Enforcer technology ensures that only the right, well formed Modbus TCP or EtherNet/IP commands from approved devices can pass through the firewall.
Known as "Deep Packet Inspection", this prevents incidents ranging from inappropriate remote programming to deliberately corrupted messages from malware and hackers. Technology like this is a rare capability amongst firewalls.
Ease of use for engineers extends to making it possible to implement firewall rules by selecting use cases, rather than having to know protocol specific nuances. For example, if you want the ConneXium Tofino Firewall to only allow EtherNet/IP Data Read commands to pass between a PLC and an HMI, then you select the Read Only option. You don’t have to understand the complex lists of commands, objects and services that are defined in the EtherNet/IP and CIP specifications.
Industrial Security that Just Works
Whether the ConneXium Tofino Firewall is a product you would consider or not, I hope this information shows how technology can be designed to make industrial cyber security easy to deploy. Whether you use Tofino Enforcer technology or not, we hope that you can see how cyber security technology can be delivered so controls professionals can ensure their systems are secure - and still concentrate on their core responsibilities of safe and reliable production.
I will close with some words from Bob Lockhart, a senior industry analyst from Navigant/Pike Research:
"Automation systems face unique cyber security challenges that require protection, built by companies that understand how those systems work.... Companies want to focus on their core business, not the enabling technology."
We feel that the ConneXium Tofino Firewall goes a long way to securing systems without engineers having to become firewall gurus. Whether or not you use ours or Schneider Electric’s products, I hope that this article helps convince you that industrial cyber security does not have to be complicated.
What are the complexities you face in implementing cyber security in your facility? Let us know your thoughts.
Related Content to Download
|
Technical Briefing Kit - "Understanding Deep Packet Inspection for SCADA Security"
|
Related Links
- Press Release: Belden Assists Schneider Electric to Secure Critical Industrial Automation Systems
- Blog: SCADA Security & Deep Packet Inspection – Part 1 of 2
- Blog: SCADA Security & Deep Packet Inspection – Part 2 of 2
- Blog: #1 ICS and SCADA Security Myth: Protection by Air Gap



Add new comment