The Critical SCADA Security Patch that your Control System Isn’t Getting
Yesterday afternoon I received a note from another security expert that has left me a bit stunned. Like most of you, I assumed that if you are patching your Windows computers on your SCADA or ICS system (using some variation of Microsoft Windows Update), then any vulnerable services that can be patched will be patched. Well guess again – you may still have a number of open vulnerabilities that are happily being missed by the Windows update service. And scariest of all, you can’t do much about it.
PCs on the plant floor that are NOT running Microsoft products such as Microsoft Office did not automatically receive updates for two serious vulnerabilities.
Photo courtesy of Lewis Technical Engineering LLC.
Welcome to the Wild World of Windows Common Controls
To understand why this is possible, it helps to know a little about something called Windows Common Controls. Common Controls are executable routines that Microsoft supplies to give applications from different developers for a unified look and feel. For example, the Tool Tip Control creates those small rectangular windows that display help text when you place the cursor over some button or tab and wait for few milliseconds.
Common Controls have been in use from the early days of Windows. Applications like Word or SQL Server use them extensively, but so do many developers of 3rd party applications. In the SCADA and ICS world, it is a fair guess that the bulk of the software developed for industrial server or client applications on Windows machines use them.
You Can Have the Patch IF…
The problem started when Microsoft announced the existence of two serious vulnerabilities (MS12-027 and MS12-060) in the ActiveX controls contained in the file MSCOMCTL.OCX. According to the Common Vulnerabilities and Exposures (CVE) database, these flaws were being exploited as targeted attacks in April 2012 using specially crafted malicious RTF files sent via email.
Microsoft soon provided patches to fix these vulnerabilities in their April and August patch releases. And that is when the fun started.
It seems that the Windows Update service will deliver the patches ONLY when qualifying Microsoft products, such as MS Office, are detected. If your computer isn’t running an application like MS Office, Microsoft SQL Server or Microsoft BizTalk Server, it won’t get patched. It doesn’t matter if your computer has a critical SCADA application that uses the vulnerable OCX file, you are out of luck. No patch for you.
To make matters worse, even standalone updates from Microsoft fail during installation unless the qualifying Microsoft product is detected. And tools like Microsoft Baseline Security Analyzer (MBSA) will miss this as well, because as soon as MSBA sees that you don’t have the qualifying application (e.g. MS Office) installed, it doesn’t bother to check if the MSCOMCTL.OCX file is current. It just quits.
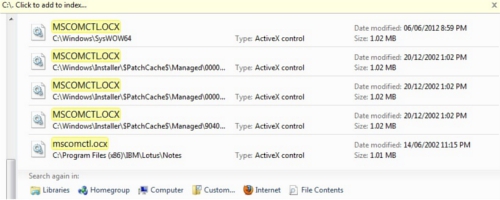
How to Check if a PC has the Vulnerabilities
- Search C: drive for the file MSCOMCTL.OCX.
- Note the date stamp of the file.
- If the copy in C:\Windows32\System is before May 2012, then your computer is unpatched. In the screen shot shown above, the computer has been patched since the file date is June 2012.
- If there are other copies that are from before May 2012, then the related application may be running a vulnerable version, even though the computer has been patched. In the screen shot above, there is one application (Lotus Notes) that may have the vulnerabilities.
As I noted above, these Windows Common Controls were extensively used in many SCADA and ICS products. Yet very few computers in industrial automation settings run applications like Microsoft Office. A few running Microsoft SQL Server will get patched, but 99% of the SCADA and ICS computers will not get this critical patch. Furthermore, by design a vulnerable common control delivered by Product X can be used by other applications and thus potentially exploited in Product Z.
According to MS12-060 FAQ, Independent Software Vendors (ISVs) that have products using the Windows Common Controls should repackage their product with the latest updates. But how many ICS vendors will do that? And how many control system users will install that update in a timely manner?
Remember, this likely won’t be an automatic update of a single file – it could be a new package to install. And, even if the patch is available, it needs to be tested and certified. My guess is that the SCADA/ICS world is facing a situation where there will be a massive number of unpatched and vulnerable computers running on critical systems for the next year or two. I don’t think that is good news.
Patching for ICS and SCADA Security is Broken
To me this is another example of how the entire strategy of patching for SCADA and ICS security is broken. Vendors are reluctant to supply patches for many control products (especially legacy products), and users are reluctant to deploy patches when they get them. Furthermore, even when you think you are patching your system, you might not be.
It is time we moved beyond the dream that the continuous race to patch, that we live with on our personal computers, will work on the plant floor. Over the next few months I plan to talk about what I see as alternatives to patching.
Given this information, what are you going to do about the Windows PCs on your plant floor? All tips are welcome!
Related Content to Download
|
White Paper: "Using ANSI/ISA-99 Standards to Improve Control System Security" |
Related Links
- Microsoft webpage: Microsoft Security Bulletin MS12-027 – Critical
- Microsoft webpage: Microsoft Security Bulletin MS12-060 – Critical
- Common Vulnerabilities and Exposures (CVE) webpage: CVE-2012-0158
- Threatpost.com webpage: Microsoft Patches Critical MS12-060 Office Flaw Being Used in Targeted Attacks
- Blog: SCADA Security: A Call-out to Control Engineers about Air Gaps




Comments
Excellent Post!
Great job, Eric! Really a useful/practical post for execs and technicians to read and get a sense of the issues faced by industries and facilities using ICS.
What I especially like about the posting is it also provides a "how to" for plant managers and their teams to check for current vulnerabilities.
Anyway, well done! Very Helpful!
Ernie Hayden CISSP CEH
Good point
Good you raised this point. Many security assessments miss this because consultants are not aware of the s/w components used. Very similar to those consultants that identify vulnerabilities exclusively with the use of tools like Nessus and MBSA. They miss many SCADA components and their vulnerabilities because either plug-ins are missing or the way it is checked.
Other sub-components exist that have vulnerabilities not patched. They can only be identified by systematically checking s/w components and their version number. However sometimes vendors use their own version numbers which hides the true state of this software.
But you are right the average system has more vulnerabilities then stakeholders are aware of.
Patching options
Thanks for the great analysis. One thing I still don't understand - if I have machines in this class, how do I update them? It appears that you are not sure either - but it never hurts to ask!
All the best,
Brian
Helpful
Thanks Eric. Very helpful.
What About Viewers?
We load Microsoft Excell and Word "Viewers" on all our HMI nodes, would this be one of the qualified applications that would ensure updates occur?
Geoffrey Uys
Automation Engineer
What About Viewers?
Good question - my guess is that they might not be, as these applications are not listed in the MS12-027 or MS12-060 notice. We will try to confirm and post an answer.
If you or anyone else finds an answer before we do, either though Microsoft or through a bit of experimentation, please post an answer.
Add new comment