S4 SCADA Security Symposium Takeaway: Time for a Revolution
I am flying home from Digital Bond’s S4 SCADA Security Symposium as I write this (BTW this was a stellar event where, even as a security expert, I learnt an amazing amount). After listening to two days of excellent, but scary talks, the first thing that comes to mind is “SCADA/ICS security is in worse shape than I thought”. Much worse shape…
You have probably already read about the “Firesheep / Project Basecamp” ICS/SCADA disclosures, so I will not repeat that information here. Instead I want to discuss another talk that was little reported, but really shocked me. It is Sean McBride’s “The 'Lost' Decade: An Empirical Analysis of ICS-Specific Vulnerabilities since 2001”.
ICS Security is in Worse Shape than I Thought
|
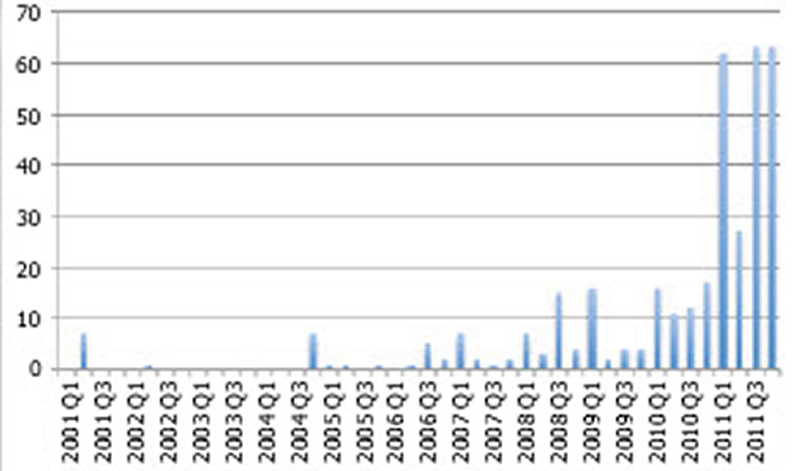
Sean presented an analysis of the publicly disclosed ICS vulnerabilities since 2001 – an avalanche of revealing statistics on how ICS vendors are dealing with security problems. It is no secret that 2011 was a bad year for publically disclosed vulnerabilities, but Sean made the pain clear – 215 ICS vulnerabilities in the last 12 months. That is more vulnerabilities than the previous decade. Plus, in Sean’s words “The public disclosures barely scratch the surface of the vulnerabilities that actually exist”. |
ICS Specific Vulnerabilities in the Public 2001-2011 (by quarter). *Slide 25 from the presentation “Documenting the ‘Lost Decade’ An Empirical Analysis of publicly disclosed ICS vulnerabilities since 2001” by Sean McBride. |
Now maybe the news wouldn’t be so bad if the ICS vendors were like the IT vendors and fixed these bugs, but it appears that many are not. Less than half of the 364 public vulnerabilities have patches available. Some ICS companies simply don’t appear to care.
Advantech has 12 public vulnerabilities (half with exploits), and only one patch available. If I was an Advantech customer I would be screaming at them, while installing firewalls and IDS (Intrustion Detection System) equipment as fast as I could.
Even when there are patches, many are useless. Sean quoted an ICS-CERT presentation from FIRST 2011
“ICS-CERT has seen a 60% failure [rate] in patches fixing the reported vulnerability!”
A few companies bucked the trend and were praised by Sean for their response to vulnerabilities:
- Honeywell - for informing its customers about the vulnerabilities in the bundled Rockwell EDS Hardware Installation Tool that is shipped with every Experion system.
- 7-Technologies - (a division of Schneider) for patching 16 out of 17 vulnerabilities.
But for the most part, vendors performed poorly when it came to addressing vulnerabilities, even when their products have public exploits.
Why Aren’t Vendors Getting the Message?
Sean’s analysis is concerning, and not just for the obvious fact that we have a lot of insecure ICS/SCADA product in the field. It appears that many vendors are either not taking this seriously or don’t know how to.
Dale Peterson’s (Founder and CEO of Digitalbond and the S4 Conference) stated reason for disclosing the flood of ICS vulnerabilities at S4 (via the now infamous “Project Basecamp: Hacking and Exploiting PLCs” talk) was to scare the vendors into moving on security. But looking at the statistics, I am not sure the tactic will work.
In 2011 too many vendors were informed of vulnerabilities in public, didn’t hear their customers yelling, and went back to sleep. The result? The security community knows there is a problem, and the bad guys know there is an opportunity, but the end users are still in the dark.
Now if you are reading this blog, you are probably one of the ICS/SCADA users who are not in the dark. You care about security and you want to do something about it. Unfortunately, either there aren’t enough of you, or you’re not telling the vendors that security matters via your RFPs.
Spread the message to your fellow End Users and Control Engineers that ICS security is vital. Tell your vendors you expect secure products. Tell your purchasing departments to make good security practices a condition of sale. It doesn’t matter if you tweet, blog, write a memo or talk over a coffee. Just get the message out. Start the revolution for more secure control systems.
Related Content to Download
Note: you need to be a member of tofinosecurity.com and logged in to have access to the document below. Register here to become a member.
|
Presentation - "Documenting the 'Lost Decade'" |
Related Links regarding S4 Disclosures
-
Wired.com: Hoping to Teach a Lesson, Researchers Release Exploits for Critical Infrastructure Software
-
Threatpost.com: UPDATE: Looking For a 'FireSheep' Moment, Researchers Lay Bare Woeful SCADA Security
-
Networkworld.com: Firesheep moment for SCADA: Hacking critical infrastructure systems now as easy as pushing a button?
Related Links from Practical SCADA Security
-
Schneider Vulnerabilities: Where are the ICS/SCADA End Users?
-
SCADA Cyber Security Problems – Just How Common are the Programming Errors?
-
Honeywell Leads ICS and SCADA World with First ISASecure Certification



Comments
Why Vendors Don't Secure
Vendors do not secure their products because users don't ask them to. Users do not ask for security because there is no regulation that says they should.
No-one has responsibility. They do not have responsibility because no-one has assigned it.
Until regulations formally assign responsibility for security in a product to the appropriate people, this problem will continue to fester.
Great blog.
Great blog.
Add new comment